Certified Ethical Hacker Exam (CEH v12) Free Questions - Part 7
Question No : 91) John, a security analyst working for an organization, found a critical vulnerability on the organization's LAN that allows him to view financial and personal information about the rest of the employees. Before reporting the vulnerability, he examines the information shown by the vulnerability for two days without disclosing any information to third parties or other internal employees. He does so out of curiosity about the other employees and may take advantage of this information later. What would John be considered as?
A. Cybercriminal
B. Black hat
C. White hat
D. Gray hat
Question No : 92) Log monitoring tools performing behavioral analysis have alerted several suspicious logins on a Linux server occurring during non-business hours. After further examination of all login activities, it is noticed that none of the logins have occurred during typical work hours. A Linux administrator who is investigating this problem realizes the system time on the Linux server is wrong by more than twelve hours. What protocol used on Linux servers to synchronize the time has stopped working?
A. Time Keeper
B. NTP
C. PPP
D. OSPP
Question No : 93) Mr. Omkar performed tool-based vulnerability assessment and found two vulnerabilities. During analysis, he found that these issues are not true vulnerabilities. What will you call these issues?
A. False positives
B. True negatives
C. True positives
D. False negatives
Question No : 94) Which among the following is the best example of the third step (delivery) in the cyber kill chain?
A. An intruder sends a malicious attachment via email to a target.
B. An intruder creates malware to be used as a malicious attachment to an email.
C. An intruder's malware is triggered when a target opens a malicious email attachment.
D. An intruder's malware is installed on a target's machine.
Question No : 95) Which mode of IPSec should you use to assure security and confidentiality of data within the same LAN?
A. ESP transport mode
B. ESP confidential
C. AH permiscuous
D. AH Tunnel mode
Question No : 96) The network users are complaining because their system are slowing down. Further, every time they attempt to go a website, they receive a series of pop-ups with advertisements. What types of malware have the system been infected with?
A. Virus
B. Spyware
C. Trojan
D. Adware
Question No : 97) Scenario1:
1.Victim opens the attacker's web site.
2.Attacker sets up a web site which contains interesting and attractive content like 'Do you want to make
$1000 in a day?'.
3.Victim clicks to the interesting and attractive content URL.
4.Attacker creates a transparent 'iframe' in front of the URL which victim attempts to click, so victim thinks that he/she clicks to the 'Do you want to make $1000 in a day?' URL but actually he/she clicks to the content or URL that exists in the transparent 'iframe' which is setup by the attacker.
What is the name of the attack which is mentioned in the scenario?
A. Session Fixation
B. HTML Injection
C. HTTP Parameter Pollution
D. Clickjacking Attack
Question No : 98) Which of the following Metasploit post-exploitation modules can be used to escalate privileges on Windows systems?
A. getsystem
B. getuid
C. keylogrecorder
D. autoroute
Question No : 99) in an attempt to increase the security of your network, you Implement a solution that will help keep your wireless network undiscoverable and accessible only to those that know It. How do you accomplish this?
A. Delete the wireless network
B. Remove all passwords
C. Lock all users
D. Disable SSID broadcasting
Question No : 100) _________ is a type of phishing that targets high-profile executives such as CEOs, CFOs, politicians, and celebrities who have access to confidential and highly valuable information.
A. Spear phishing
B. Whaling
C. Vishing
D. Phishing
Question No : 101) What did the following commands determine?
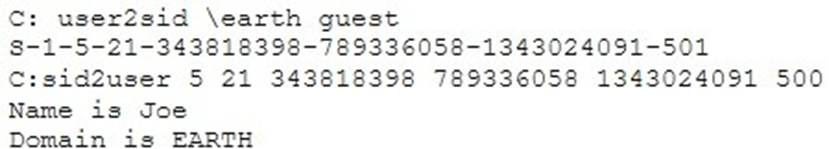
A. That the Joe account has a SID of 500
B. These commands demonstrate that the guest account has NOT been disabled
C. These commands demonstrate that the guest account has been disabled
D. That the true administrator is Joe
E. Issued alone, these commands prove nothing
Question No : 102) Although FTP traffic is not encrypted by default, which layer 3 protocol would allow for end- to-end encryption of the connection?
A. SFTP
B. Ipsec
C. SSL
D. FTPS
Question No : 103) Which of the following scanning method splits the TCP header into several packets and makes it difficult for packet filters to detect the purpose of the packet?
A. ACK flag probe scanning
B. ICMP Echo scanning
C. SYN/FIN scanning using IP fragments
D. IPID scanning
Question No : 104) An attacker utilizes a Wi-Fi Pineapple to run an access point with a legitimate-looking SSID for a nearby business in order to capture the wireless password. What kind of attack is this?
A. MAC spoofing attack
B. Evil-twin attack
C. War driving attack
D. Phishing attack
Question No : 105) Which of the following Bluetooth hacking techniques does an attacker use to send messages to users without the recipient?s consent, similar to email spamming?
A. Bluesmacking
B. BlueSniffing
C. Bluejacking
D. Bluesnarfing
312-50v12 Answers