CompTIA Security+Exam (SY0-701) Free Questions - Part 18
Question No : 256) An attacker has successfully exfiltrated several non-salted password hashes from an online system. Given the logs below:
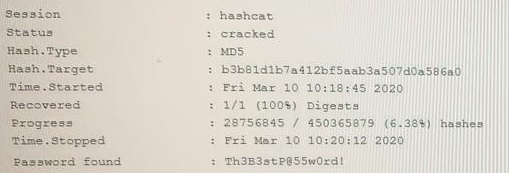
Which of the following BEST describes the type of password attack the attacker is performing?
A. Dictionary
B. Pass-the-hash
C. Brute-force
D. Password spraying
Question No : 257) A security analyst sees the following log output while reviewing web logs:

A. Secure cookies
B. Input validation
C. Code signing
D. Stored procedures
Question No : 258) Under GDPR, which of the following is MOST responsible for the protection of privacy and website user rights?
A. The data protection officer
B. The data processor
C. The data owner
D. The data controller
Question No : 259) A user is concerned that a web application will not be able to handle unexpected or random input without crashing. Which of the following BEST describes the type of testing the user should perform?
A. Code signing
B. Fuzzing
C. Manual code review
D. Dynamic code analysis
Question No : 260) A user recently attended an exposition and received some digital promotional materials The user later noticed blue boxes popping up and disappearing on the computer, and reported receiving several spam emails, which the user did not open Which of the following is MOST likely the cause of the reported issue?
A. There was a drive-by download of malware
B. The user installed a cryptominer
C. The OS was corrupted
D. There was malicious code on the USB drive
Question No : 261) Which of the following would be the BEST resource lor a software developer who is looking to improve secure coding practices for web applications?
A. OWASP
B. Vulnerability scan results
C. NIST CSF
D. Third-party libraries
Question No : 262) Which of the following control sets should a well-written BCP include? (Select THREE)
A. Preventive
B. Detective
C. Deterrent
D. Corrective
E. Compensating
F. Physical
G. Recovery
Question No : 263) The website http://companywebsite.com requires users to provide personal Information, Including security question responses, for registration. Which of the following would MOST likely cause a data breach?
A. Lack of input validation
B. Open permissions
C. Unsecure protocol
D. Missing patches
Question No : 264) A security engineer at an offline government facility is concerned about the validity of an SSL certificate. The engineer wants to perform the fastest check with the least delay to determine if the certificate has been revoked. Which of the following would BEST these requirement?
A. RA
B. OCSP
C. CRL
D. CSR
Question No : 265) An organization's Chief Security Officer (CSO) wants to validate the business's involvement in the incident response plan to ensure its validity and thoroughness. Which of the following will the CSO MOST likely use?
A. An external security assessment
B. A bug bounty program
C. A tabletop exercise
D. A red-team engagement
Question No : 266) A network technician is installing a guest wireless network at a coffee shop. When a customer purchases an Item, the password for the wireless network is printed on the recent so the customer can log in. Which of the following will the technician MOST likely configure to provide the highest level of security with the least amount of overhead?
A. WPA-EAP
B. WEP-TKIP
C. WPA-PSK
D. WPS-PIN
Question No : 267) Which of the following job roles would sponsor data quality and data entry initiatives that ensure business and regulatory requirements are met?
A. The data owner
B. The data processor
C. The data steward
D. The data privacy officer.
Question No : 268) A security analyst is configuring a large number of new company-issued laptops. The analyst received the following requirements:
? The devices will be used internationally by staff who travel extensively.
? Occasional personal use is acceptable due to the travel requirements.
? Users must be able to install and configure sanctioned programs and productivity suites.
? The devices must be encrypted
? The devices must be capable of operating in low-bandwidth environments.
Which of the following would provide the GREATEST benefit to the security posture of the devices?
A. Configuring an always-on VPN
B. Implementing application whitelisting
C. Requiring web traffic to pass through the on-premises content filter
D. Setting the antivirus DAT update schedule to weekly
Question No : 269) A critical file server is being upgraded and the systems administrator must determine which RAID level the new server will need to achieve parity and handle two simultaneous disk failures. Which of the following RAID levels meets this requirements?
A. RAID 0+1
B. RAID 2
C. RAID 5
D. RAID 6
Question No : 270) Due to unexpected circumstances, an IT company must vacate its main office, forcing all operations to alternate, off-site locations Which of the following will the company MOST likely reference for guidance during this change?
A. The business continuity plan
B. The retention policy
C. The disaster recovery plan
D. The incident response plan
SY0-701 Answers