CompTIA Security+Exam (SY0-701) Free Questions - Part 33
Question No : 481) An organization recently discovered that a purchasing officer approved an invoice for an amount that was different than the original purchase order. After further investigation a security analyst determines that the digital signature for the fraudulent invoice is exactly the same as the digital signature for the correct invoice that had been approved Which of the following attacks MOST likely explains the behavior?
A. Birthday
B. Rainbow table
C. Impersonation
D. Whaling
Question No : 482) Which of the following should a data owner require all personnel to sign to legally protect intellectual property?
A. An NDA
B. An AUP
C. An ISA
D. An MOU
Question No : 483) Which of the following terms should be included in a contract to help a company monitor the ongoing security maturity of a new vendor?
A. A right-to-audit clause allowing for annual security audits
B. Requirements for event logs to be kept for a minimum of 30 days
C. Integration of threat intelligence in the company's AV
D. A data-breach clause requiring disclosure of significant data loss
Question No : 484) A security analyst was called to Investigate a file received directly from a hardware manufacturer. The analyst is trying to determine whether the file was modified in transit before installation on the user's computer. Which of the following can be used to safely assess the file?
A. Check the hash of the installation file
B. Match the file names
C. Verify the URL download location
D. Verify the code-signing certificate
Question No : 485) A security analyst is concerned about critical vulnerabilities that have been detected on some applications running inside containers. Which of the following is the BEST remediation strategy?
A. Update the base container image and redeploy the environment.
B. Include the containers in the regular patching schedule for servers
C. Patch each running container individually and test the application
D. Update the host in which the containers are running
Question No : 486) A security administrator needs to inspect in-transit files on the enterprise network to search for Pll, credit card data, and classification words. Which of the following would be the BEST to use?
A. IDS solution
B. EDR solution
C. HIPS software solution
D. Network DLP solution
Question No : 487) A penetration tester successfully gained access to a company's network The investigating analyst determines malicious traffic connected through the WAP despite filtering rules being in place. Logging in to the connected switch, the analyst sees the following m the ARP table:
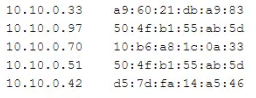
Which of the following did the penetration tester MOST likely use?
A. ARP poisoning
B. MAC cloning
C. Man in the middle
D. Evil twin
Question No : 488) Which of the following BEST reduces the security risks introduced when running systems that have expired vendor support and lack an immediate replacement?
A. Implement proper network access restrictions
B. Initiate a bug bounty program
C. Classify the system as shadow IT.
D. Increase the frequency of vulnerability scans
Question No : 489) Which of the following uses six initial steps that provide basic control over system security by including hardware and software inventory, vulnerability management, and continuous monitoring to minimize risk in all network environments?
A. ISO 27701
B. The Center for Internet Security
C. SSAE SOC 2
D. NIST Risk Management Framework
Question No : 490) A company Is concerned about is security after a red-team exercise. The report shows the team was able to reach the critical servers due to the SMB being exposed to the Internet and running NTLMV1, Which of the following BEST explains the findings?
A. Default settings on the servers
B. Unsecured administrator accounts
C. Open ports and services
D. Weak Data encryption
Question No : 491) Joe, an employee, is transferring departments and is providing copies of his files to a network share folder for his previous team to access. Joe is granting read-write-execute permissions to his manager but giving read-only access to the rest of the team. Which of the following access controls is Joe using?
A. FACL
B. DAC
C. ABAC
D. MAC
Question No : 492) Which of the following control types is focused primarily on reducing risk before an incident occurs?
A. Preventive
B. Deterrent
C. Corrective
D. Detective
Question No : 493) A company currently uses passwords for logging in to company-owned devices and wants to add a second authentication factor. Per corporate policy, users are not allowed to have smartphones at their desks. Which of the following would meet these requirements?
A. Smart card
B. PIN code
C. Knowledge-based question
D. Secret key
Question No : 494) The security team received a report of copyright infringement from the IP space of lire corporate network. The report provided a precise time stamp for the incident as well as the name of the copyrighted le. The analyst has been tasked with determining the infringing source machine and instructed to implement measures to prevent such incidents from occurring again. Which of the following is MOST capable of accomplishing both tasks?
A. HIDS
B. Allow list
C. TPM
D. NGFW
Question No : 495) Which of the following environments minimizes end user disruption and is MOST likely to be used to assess the impacts of any database migrations or major system changes by using the final version of the code in an operationally representative environment?
A. Staging
B. Test
C. Production
D. Development
SY0-701 Answers