CompTIA Security+Exam (SY0-701) Free Questions - Part 29
Question No : 421) A multinational organization that offers web-based services has datacenters that are located only in the United States; however, a large number of its customers are in Australia, Europe, and China. Payments for services are managed by a third party in the United Kingdom that specializes in payment gateways. The management team is concerned the organization is not compliant with privacy laws that cover some of its customers. Which of the following frameworks should the management team follow?
A. Payment Card Industry Data Security Standard
B. Cloud Security Alliance Best Practices
C. ISO/IEC 27032 Cybersecurity Guidelines
D. General Data Protection Regulation
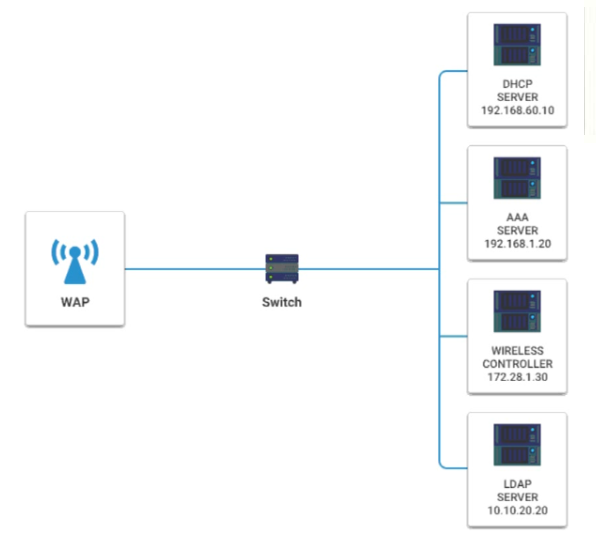
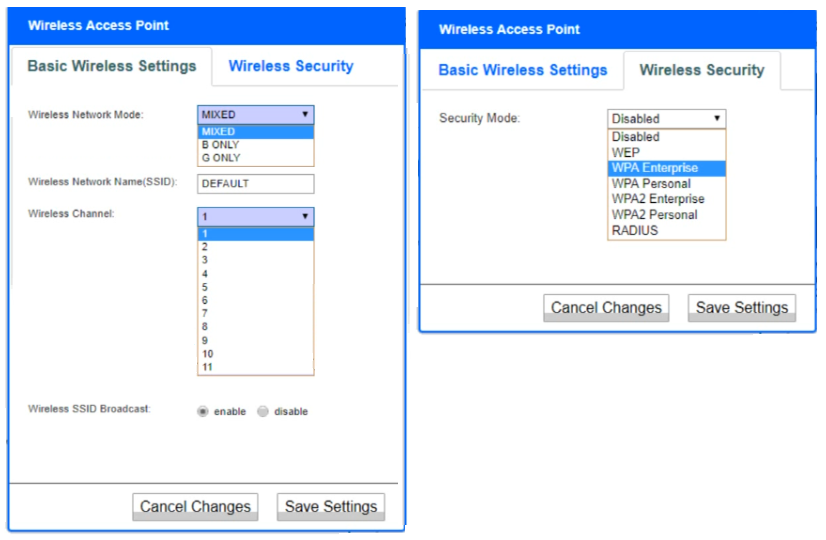
Question No : 422) A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
WAP
DHCP Server
AAA Server
Wireless Controller
LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Question No : 423) A security analyst notices several attacks are being blocked by the NIPS but does not see anything on the boundary firewall logs. The attack seems to have been thwarted Which of the following resiliency techniques was applied to the network to prevent this attack?
A. NIC Teaming
B. Port mirroring
C. Defense in depth
D. High availability
E. Geographic dispersal
Question No : 424) A systems administrator is troubleshooting a server's connection to an internal web server. The administrator needs to determine the correct ports to use. Which of the following tools BEST shows which ports on the web server are in a listening state?
A. Ipconfig
B. ssh
C. Ping
D. Netstat
Question No : 425) A financial institution would like to store its customer data in a cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would BEST meet the requirement?
A. Asymmetric
B. Symmetric
C. Homomorphic
D. Ephemeral
Question No : 426) Per company security policy, IT staff members are required to have separate credentials to perform administrative functions using just-in-time permissions. Which of the following solutions is the company Implementing?
A. Privileged access management
B. SSO
C. RADIUS
D. Attribute-based access control
Question No : 427) An organization's corporate offices were destroyed due to a natural disaster, so the organization is now setting up offices in a temporary work space. Which of the following will the organization MOST likely consult?
A. The business continuity plan
B. The disaster recovery plan
C. The communications plan
D. The incident response plan
Question No : 428) The Chief Technology Officer of a local college would like visitors to utilize the school's WiFi but must be able to associate potential malicious activity to a specific person. Which of the following would BEST allow this objective to be met?
A. Requiring all new, on-site visitors to configure their devices to use WPS
B. Implementing a new SSID for every event hosted by the college that has visitors
C. Creating a unique PSK for every visitor when they arrive at the reception area
D. Deploying a captive portal to capture visitors' MAC addresses and names
Question No : 429) Which of the following BEST describes the method a security analyst would use to confirm a file that is downloaded from a trusted security website is not altered in transit or corrupted using a verified checksum?
A. Hashing
B. Salting
C. Integrity
D. Digital signature
Question No : 430) A malware attack has corrupted 30TB of company data across all file servers A systems administrator Identifies the malware and contains the Issue, but the data Is unrecoverable. The administrator Is not concerned about the data loss because the company has a system in place that will allow users to access the data that was backed up last night. Which of the following resiliency techniques did the administrator MOST likely use to prevent impacts to business operations after an attack?
A. Tape backups
B. Replication
C. RAID
D. Cloud storage
Question No : 431) As part of a security compliance assessment, an auditor performs automated vulnerability scans. In addition, which of the following should the auditor do to complete the assessment?
A. User behavior analysis
B. Packet captures
C. Configuration reviews
D. Log analysis
Question No : 432) Which of the following is a reason why an organization would define an AUP?
A. To define the lowest level of privileges needed for access and use of the organization's resources
B. To define the set of rules and behaviors for users of the organization's IT systems
C. To define the intended partnership between two organizations
D. To define the availability and reliability characteristics between an IT provider and consumer
Question No : 433) A security analyst is investigating some users who are being redirected to a fake website that resembles www.comptia.org. The following output was found on the naming server of the organization:
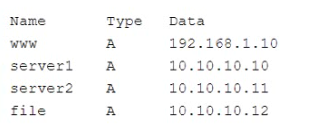
Which of the following attacks has taken place?
A. Domain reputation
B. Domain hijacking
C. Disassociation
D. DNS poisoning
Question No : 434) During an asset inventory, several assets, supplies, and miscellaneous items were noted as missing. The security manager has been asked to find an automated solution to detect any future theft of equipment. Which of the following would be BEST to implement?
A. Badges
B. Fencing
C. Access control vestibule
D. Lighting
E. Cameras
Question No : 435) A security engineer needs to build a solution to satisfy regulatory requirements that state certain critical servers must be accessed using MFA. However, the critical servers are older and are unable to support the addition of MFA. Which of the following will the engineer MOST likely use to achieve this objective?
A. A forward proxy
B. A stateful firewall
C. A jump server
D. A port tap
SY0-701 Answers