CompTIA Security+Exam (SY0-701) Free Questions - Part 27
Question No : 391) Which of the following describes a maintenance metric that measures the average time required to troubleshoot and restore failed equipment?
A. RTO
B. MTBF
C. MTTR
D. RPO
Question No : 392) A major political party experienced a server breach. The hacker then publicly posted stolen internal communications concerning campaign strategies to give the opposition party an advantage. Which of the following BEST describes these threat actors?
A. Semi-authorized hackers
B. State actors
C. Script kiddies
D. Advanced persistent threats
Question No : 393) Which of the following BEST describes a social-engineering attack that relies on an executive at a small business visiting a fake banking website where credit card and account details are harvested?
A. Whaling
B. Spam
C. Invoice scam
D. Pharming
Question No : 394) A Chief Information Officer receives an email stating a database will be encrypted within 24 hours unless a payment of $20,000 is credited to the account mentioned In the email. This BEST describes a scenario related to:
A. whaling.
B. smishing.
C. spear phishing
D. vishing
Question No : 395) A SOC is currently being outsourced. Which of the following is being used?
A. Microservices
B. SaaS
C. MSSP
D. PaaS
Question No : 396) A hospital's administration is concerned about a potential loss of patient data that is stored on tablets. A security administrator needs to implement controls to alert the SOC any time the devices are near exits. Which of the following would BEST achieve this objective?
A. Geotargeting
B. Geolocation
C. Geotagging
D. Geofencing
Question No : 397) A security engineer is installing a WAF to protect the company?s website from malicious web requests over SSL. Which of the following is needed to meet the objective?
A. A reverse proxy
B. A decryption certificate
C. A split-tunnel VPN
D. Load-balanced servers
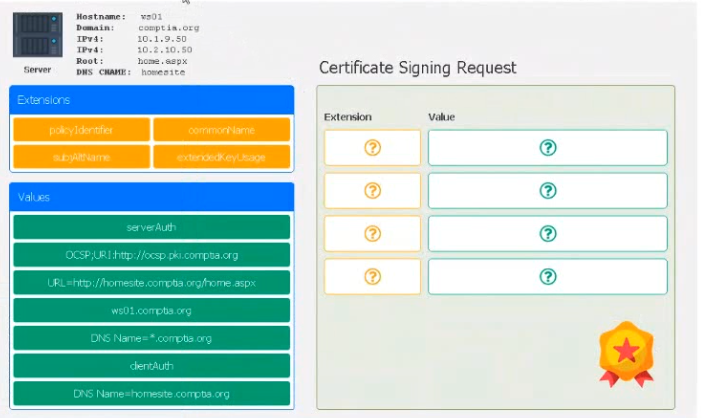
Question No : 398) Leveraging the information supplied below, complete the CSR for the server to set up TLS (HTTPS)
? Hostname: ws01
? Domain: comptia.org
? IPv4: 10.1.9.50
? IPV4: 10.2.10.50
? Root: home.aspx
? DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria
belong in the let hand column and values belong in the corresponding row in the right hand
column.
Question No : 399) A security researcher is attempting to gather data on the widespread use of a Zero-day exploit. Which of the following will the researcher MOST likely use to capture this data?
A. A DNS sinkhole
B. A honeypot
C. A vulnerability scan
D. CVSS
Question No : 400) An external forensics investigator has been hired to investigate a data breach at a large enterprise with numerous assets. It is known that the breach started in the DMZ and moved to the sensitive information, generating multiple logs as the attacker traversed through the network. Which of the following will BEST assist with this investigation?
A. Perform a vulnerability scan to identity the weak spots.
B. Use a packet analyzer to Investigate the NetFlow traffic.
C. Check the SIEM to review the correlated logs.
D. Require access to the routers to view current sessions.
Question No : 401) A security analyst is investigating multiple hosts that are communicating to external IP addresses during the hours of 2:00 a.m - 4:00 am. The malware has evaded detection by traditional antivirus software. Which of the following types of malware is MOST likely infecting the hosts?
A. RAT
B. Ransomware
C. Logic bomb
D. A worm
Question No : 402) Which of the following would satisfy three-factor authentication?
A. Password, retina scanner, and NFC card
B. Password, fingerprint scanner, and retina scanner
C. Password, hard token, and NFC card
D. Fingerprint scanner, hard token, and retina scanner
Question No : 403) As part of a company's ongoing SOC maturation process, the company wants to implement a method to share cyberthreat intelligence data with outside security partners. Which of the following will the company MOST likely implement?
A. TAXII
B. TLP
C. TTP
D. STIX
Question No : 404) The website http://companywebsite.com requires users to provide personal information including security responses, for registration. which of the following would MOST likely cause a date breach?
A. LACK OF INPUT VALIDATION
B. OPEN PERMISSIONS
C. UNSCECURE PROTOCOL
D. MISSING PATCHES
Question No : 405) An information security policy states that separation of duties is required for all highly sensitive database changes that involve customers' financial data. Which of the following will this be BEST to prevent?
A. Least privilege
B. An insider threat
C. A data breach
D. A change control violation
SY0-701 Answers