CompTIA Security+Exam (SY0-701) Free Questions - Part 28
Question No : 406) Which of the following environments utilizes dummy data and is MOST likely to be installed locally on a system that allows code to be assessed directly and modified easily with each build?
A. Production
B. Test
C. Staging
D. Development
Question No : 407) A user reports trouble using a corporate laptop. The laptop freezes and responds slowly when writing documents and the mouse pointer occasional disappears. The task list shows the following results
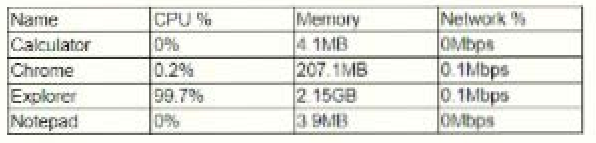
Which of the following is MOST likely the issue?
A. RAT
B. PUP
C. Spyware
D. Keylogger
Question No : 408) Which of the following corporate policies is used to help prevent employee fraud and to detect system log modifications or other malicious activity based on tenure?
A. Background checks
B. Mandatory vacation
C. Social media analysis
D. Separation of duties
Question No : 409) A company needs to validate its updated incident response plan using a real-world scenario that will test decision points and relevant incident response actions without interrupting daily operations. Which of the following would BEST meet the company's requirements?
A. Red-team exercise
B. Capture-the-flag exercise
C. Tabletop exercise
D. Phishing exercise
Question No : 410) An organization is moving away from the use of client-side and server-side certificates for EAR The company would like for the new EAP solution to have the ability to detect rogue access points. Which of the following would accomplish these requirements?
A. PEAP
B. EAP-FAST
C. EAP-TLS
D. EAP-TTLS
Question No : 411) A company is receiving emails with links to phishing sites that look very similar to the company's own website address and content. Which of the following is the BEST way for the company to mitigate this attack?
A. Create a honeynet to trap attackers who access the VPN with credentials obtained by phishing.
B. Generate a list of domains similar to the company's own and implement a DNS sinkhole for each.
C. Disable POP and IMAP on all Internet-facing email servers and implement SMTPS.
D. Use an automated tool to flood the phishing websites with fake usernames and passwords.
Question No : 412) A security architect at a large, multinational organization is concerned about the complexities and overhead of managing multiple encryption keys securely in a multicloud provider environment. The security architect is looking for a solution with reduced latency to allow the incorporation of the organization's existing keys and to maintain consistent, centralized control and management regardless of the data location Which of the following would BEST meet the architect's objectives?
A. Trusted Platform Module
B. laaS
C. HSMaaS
D. PaaS
E. Key Management Service
Question No : 413) A local coffee shop runs a small WiFi hot-spot for its customers that utilizes WPA2-PSK. The coffee shop would like to stay current with security trends and wants to implement WPA3 to make its WiFi even more secure. Which of the following technologies will the coffee shop MOST likely use in place of PSK?
A. WEP
B. MSCHAP
C. WPS
D. SAE
Question No : 414) As part of the lessons-learned phase, the SOC is tasked with building methods to detect if a previous incident is happening again. Which of the following would allow the security analyst to alert the SOC if an event is reoccurring?
A. Creating a playbook within the SOAR
B. Implementing rules in the NGFW
C. Updating the DLP hash database
D. Publishing a new CRL with revoked certificates
Question No : 415) An organization is concerned about intellectual property theft by employee who leave the organization. Which of the following will be organization MOST likely implement?
A. CBT
B. NDA
C. MOU
D. AUP
Question No : 416) A company uses specially configured workstations tor any work that requires administrator privileges to its Tier 0 and Tier 1 systems. The company follows a strict process to harden systems immediately upon delivery. Even with these strict security measures in place, an incident occurred from one of the workstations. The root cause appears to be that the SoC was tampered with or replaced. Which of the following MOST likely occurred?
A. Fileless malware
B. A downgrade attack
C. A supply-chain attack
D. A logic bomb
E. Misconfigured BIOS
Question No : 417) The board of doctors at a company contracted with an insurance firm to limit the organization?s liability. Which of the following risk management practices does the BEST describe?
A. Transference
B. Avoidance
C. Mitigation
D. Acknowledgement
Question No : 418) An organization's finance department is implementing a policy to protect against collusion. Which of the following control types and corresponding procedures should the organization implement to fulfill this policy's requirement? (Select TWO).
A. Corrective
B. Deterrent
C. Preventive
D. Mandatory vacations
E. Job rotation
F. Separation of duties
Question No : 419) An attack relies on an end user visiting a website the end user would typically visit, however, the site is compromised and uses vulnerabilities in the end users browser to deploy malicious software. Which of the blowing types of attack does this describe?
A. Smishing
B. Whaling
C. Watering hole
D. Phishing
Question No : 420) Which of the following utilize a subset of real data and are MOST likely to be used to assess the features and functions of a system and how it interacts or performs from an end user's perspective against defined test cases? (Select TWO).
A. Production
B. Test
C. Research and development
D. PoC
E. UAT
F. SDLC
SY0-701 Answers