CompTIA Security+Exam (SY0-701) Free Questions - Part 32
Question No : 466) A network administrator is concerned about users being exposed to malicious content when accessing company cloud applications. The administrator wants to be able to block access to sites based on the AUP. The users must also be protected because many of them work from home or at remote locations, providing on-site customer support. Which of the following should the administrator employ to meet these criteria?
A. Implement NAC.
B. Implement an SWG.
C. Implement a URL filter.
D. Implement an MDM.
Question No : 467) An organization has various applications that contain sensitive data hosted in the cloud. The company?s leaders are concerned about lateral movement across applications of different trust levels. Which of the following solutions should the organization implement to address the concern?
A. ISFW
B. UTM
C. SWG
D. CASB
Question No : 468) Ann, a customer, received a notification from her mortgage company stating her PII may be shared with partners, affiliates, and associates to maintain day-to-day business operations. Which of the following documents did Ann receive?
A. An annual privacy notice
B. A non-disclosure agreement
C. A privileged-user agreement
D. A memorandum of understanding
Question No : 469) Ann, a forensic analyst, needs to prove that the data she originally acquired has remained unchanged while in her custody. Which of the following should Ann use?
A. Chain of custody
B. Checksums
C. Non-repudiation
D. Legal hold
Question No : 470) A junior security analyst is conducting an analysis after passwords were changed on multiple accounts without users' interaction. The SIEM have multiple login entries with the following text:
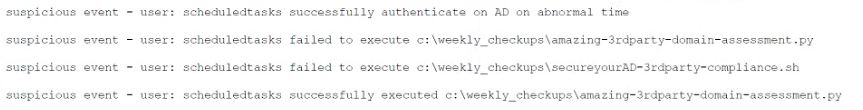
Which of the following is the MOST likely attack conducted on the environment?
A. Malicious script
B. Privilege escalation
C. Domain hijacking
D. DNS poisoning
Question No : 471) A network manager is concerned that business may be negatively impacted if the firewall in its datacenter goes offline. The manager would like to Implement a high availability pair to:
A. decrease the mean ne between failures
B. remove the single point of failure
C. cut down the mean tine to repair
D. reduce the recovery time objective
Question No : 472) While investigating a data leakage incident, a security analyst reviews access control to cloud-hosted data. The following information was presented in a security posture report.
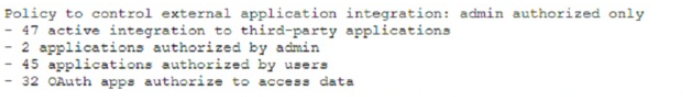
Based on the report, which of the following was the MOST likely attack vector used against the company?
A. Spyware
B. Logic bomb
C. Potentially unwanted programs
D. Supply chain
Question No : 473) A user's account is constantly being locked out. Upon further review, a security analyst found the following in the SIEM
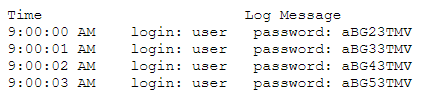
Which of the following describes what is occurring?
A. An attacker is utilizing a password-spraying attack against the account.
B. An attacker is utilizing a dictionary attack against the account.
C. An attacker is utilizing a brute-force attack against the account.
D. An attacker is utilizing a rainbow table attack against the account.
Question No : 474) A security administrator is setting up a SIEM to help monitor for notable events across the enterprise. Which of the following control types does this BEST represent?
A. Preventive
B. Compensating
C. Corrective
D. Detective
Question No : 475) During an investigation, a security manager receives notification from local authorities mat company proprietary data was found on a former employees home computer, The former employee?s corporate workstation has since been repurposed, and the data on the hard drive has been overwritten Which of the following would BEST provide the security manager with enough details to determine when the data was removed from the company network?
A. Properly congured hosts with security logging
B. Properly congured endpoint security tool with darting
C. Properly congured SIEM with retention policies
D. Properly congured USB blocker with encryption
Question No : 476) A manufacturing company has several one-off legacy information systems that cannot be migrated to a newer OS due to software compatibility issues. The Oss are still supported by the vendor, but the industrial software is no longer supported. The Chief Information Security Officer (CISO) has created a resiliency plan for these systems that will allow OS patches to be installed in a non-production environment, while also creating backups of the systems for recovery. Which of the following resiliency techniques will provide these capabilities?
A. Redundancy
B. RAID 1+5
C. Virtual machines
D. Full backups
Question No : 477) Which of the following is a risk that is specifically associated with hosting applications in the public cloud?
A. Unsecured root accounts
B. Zero day
C. Shared tenancy
D. Insider threat
Question No : 478) To mitigate the impact of a single VM being compromised by another VM on the same hypervisor, an administrator would like to utilize a technical control to further segregate the traffic. Which of the following solutions would BEST accomplish this objective?
A. Install a hypervisor firewall to filter east-west traffic.
B. Add more VLANs to the hypervisor network switches.
C. Move exposed or vulnerable VMs to the DMZ.
D. Implement a zero-trust policy and physically segregate the hypervisor servers.
Question No : 479) A security forensics analyst is examining a virtual server. The analyst wants to preserve the present state of the virtual server, including memory contents. Which of the following backup types should be used?
A. Snapshot
B. Differential
C. Cloud
D. Full
E. Incremental
Question No : 480) A user's login credentials were recently compromised During the investigation, the security analyst determined the user input credentials into a pop-up window when prompted to confirm the username and password. However the trusted website does not use a pop-up for entering user credentials. Which of the following attacks occurred?
A. Cross-site scripting
B. SQL injection
C. DNS poisoning
D. Certificate forgery
SY0-701 Answers