CompTIA Security+Exam (SY0-701) Free Questions - Part 22
Question No : 316) A security analyst is investigating a phishing email that contains a malicious document directed to the company's Chief Executive Officer (CEO). Which of the following should the analyst perform to understand the threat and retrieve possible IoCs?
A. Run a vulnerability scan against the CEOs computer to find possible vulnerabilities
B. Install a sandbox to run the malicious payload in a safe environment
C. Perform a traceroute to identify the communication path
D. Use netstat to check whether communication has been made with a remote host
Question No : 317) A recent security assessment revealed that an actor exploited a vulnerable workstation within an organization and has persisted on the network for several months. The organization realizes the need to reassess Its security. Strategy for mitigating risks within the perimeter Which of the following solutions would BEST support the organization's strategy?
A. FIM
B. DLP
C. EDR
D. UTM
Question No : 318) An engineer is setting up a VDI environment for a factory location, and the business wants to deploy a low-cost solution to enable users on the shop floor to log in to the VDI environment directly. Which of the following should the engineer select to meet these requirements?
A. Laptops
B. Containers
C. Thin clients
D. Workstations
Question No : 319) Joe. a security analyst, recently performed a network discovery to fully understand his organization's electronic footprint from a "public" perspective. Joe ran a set of commands and received the following output:
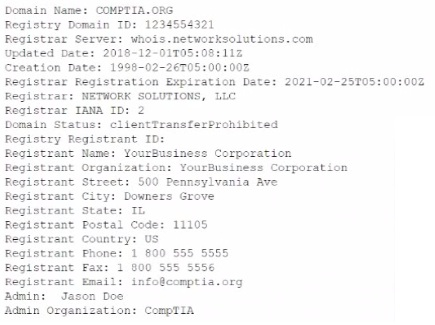
Which of the following can be determined about the organization's public presence and security posture? (Select TWO).
A. Joe used Who is to produce this output.
B. Joe used cURL to produce this output.
C. Joe used Wireshark to produce this output
D. The organization has adequate information available in public registration.
E. The organization has too much information available in public registration.
F. The organization has too little information available in public registration
Question No : 320) A security analyst has been tasked with creating a new WiFi network for the company. The requirements received by the analyst are as follows:
?Must be able to differentiate between users connected to WiFi?The encryption keys need to change routinely without interrupting the users or forcing reauthentication
?Must be able to integrate with RADIUS
?Must not have any open SSIDs
Which of the following options BEST accommodates these requirements?
A. WPA2-Enterprise
B. WPA3-PSK
C. 802.11n
D. WPS
Question No : 321) A cybersecurity administrator needs to allow mobile BYOD devices to access network resources. As the devices are not enrolled to the domain and do not have policies applied to them, which of the following are best practices for authentication and infrastructure security? (Select TWO).
A. Create a new network for the mobile devices and block the communication to the internal network and servers
B. Use a captive portal for user authentication.
C. Authenticate users using OAuth for more resiliency
D. Implement SSO and allow communication to the internal network
E. Use the existing network and allow communication to the internal network and servers.
F. Use a new and updated RADIUS server to maintain the best solution
Question No : 322) Certain users are reporting their accounts are being used to send unauthorized emails and conduct suspicious activities. After further investigation, a security analyst notices the following:
? All users share workstations throughout the day.
? Endpoint protection was disabled on several workstations throughout the network.
? Travel times on logins from the affected users are impossible.
? Sensitive data is being uploaded to external sites.
? All user account passwords were forced to be reset and the issue continued.
Which of the following attacks is being used to compromise the user accounts?
A. Brute-force
B. Keylogger
C. Dictionary
D. Rainbow
Question No : 323) A company is implementing a DLP solution on the file server. The file server has PII, financial information, and health information stored on it. Depending on what type of data that is hosted on the file server, the company wants different DLP rules assigned to the data. Which of the following should the company do to help to accomplish this goal?
A. Classify the data
B. Mask the data
C. Assign the application owner
D. Perform a risk analysis
Question No : 324) An information security officer at a credit card transaction company is conducting a framework-mapping exercise with the internal controls. The company recently established a new office in Europe. To which of the following frameworks should the security officer map the existing controls? (Select TWO).
A. ISO
B. PCI DSS
C. SOC
D. GDPR
E. CSA
F. NIST
Question No : 325) During an incident, an EDR system detects an increase in the number of encrypted outbound connections from multiple hosts. A firewall is also reporting an increase in outbound connections that use random high ports. An analyst plans to review the correlated logs to find the source of the incident. Which of the following tools will BEST assist the analyst?
A. A vulnerability scanner
B. A NGFW
C. The Windows Event Viewer
D. A SIEM
Question No : 326) Which of the following is the MOST likely reason for securing an air-gapped laboratory HVAC system?
A. To avoid data leakage
B. To protect surveillance logs
C. To ensure availability
D. To restrict remote access
Question No : 327) A security analyst needs to perform periodic vulnerably scans on production systems. Which of the following scan types would produce the BEST vulnerability scan report?
A. Port
B. Intrusive
C. Host discovery
D. Credentialed
Question No : 328) Which of the following provides a catalog of security and privacy controls related to the United States federal information systems?
A. GDPR
B. PCI DSS
C. ISO 27000
D. NIST 800-53
Question No : 329) A system that requires an operation availability of 99.99% and has an annual maintenance window available to patching and fixes will require the HIGHEST:
A. MTBF
B. MTTR
C. RPO
D. RTO
Question No : 330) A security analyst was deploying a new website and found a connection attempting to authenticate on the site's portal. While Investigating The incident, the analyst identified the following Input in the username field:
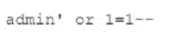
Which of the following BEST explains this type of attack?
A. DLL injection to hijack administrator services
B. SQLi on the field to bypass authentication
C. Execution of a stored XSS on the website
D. Code to execute a race condition on the server.
SY0-701 Answers